Easy-to-Learn Notation
Based on the proven data flow diagram syntax, learn the basics in minutes and start modeling immediately.

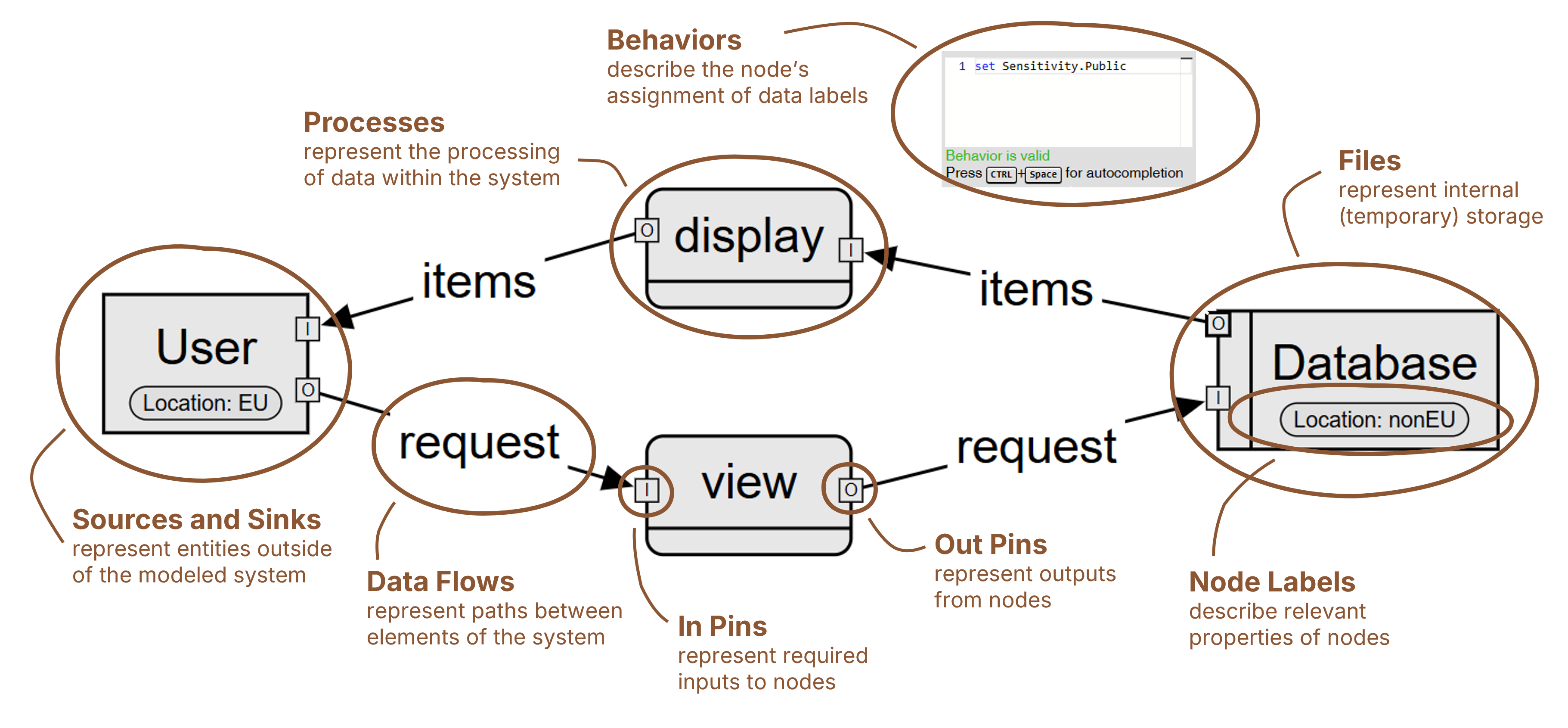
Our approach to data flow diagrams unifies previous modeling approaches and provides and concise syntax to express the information security of software systems. We build on the 1979 DeMarco notation comprising data sources, sinks, flows, and files. To enable security-related analysis, we extend the notation by input and output pins, behaviors, and means to characterize data and nodes using labels. See the wiki for more information.
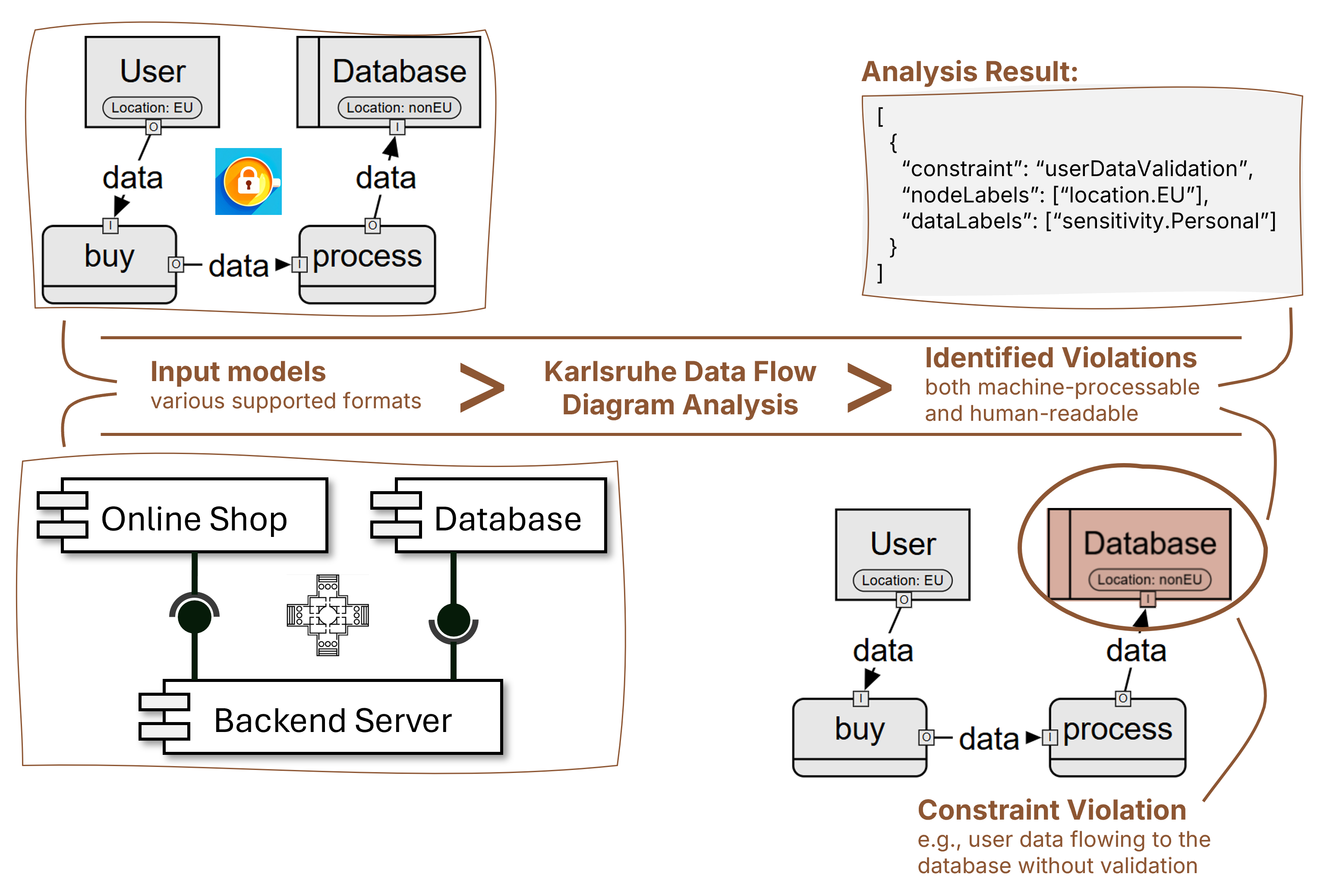
Our analysis utilizes label propagation to analyze the characteristics of data flows. First, we extract all possible flows from data flow diagrams or other model representations such as Palladio software architecture models. Afterwards, we query these so-called Transpose Flow Graphs (TFGs) to identify violations of information security requirements that were denoted as data flow constraints. Exemplary questions are:
All aspects of the xDECAF data flow analysis framework have been scientifically published at multiple conferences and journals, e.g., the data flow diagram notation, or the core analysis algorithms. For a quick overview of the analysis framework, please see this key publication:

N. Boltz and S. Hahner, et al., "An Extensible Framework for Architecture-Based Data Flow Analysis
for Information Security",
European Conference on Software Architecture (ECSA), Springer,
2024, doi: 10.1007/978-3-031-66326-0_21.
To get started quickly, you may also refer to our data flow analysis lecture that introduces all fundamental topics required to understand the xDECAF framework. This includes data flow diagrams, data and node labels, data flow constraints, flow graph extraction, and label propagation:

S. Hahner, "Data Flow Analysis", Guest Lecture, Software Security Engineering, Karlsruhe Institute of Technology (KIT).